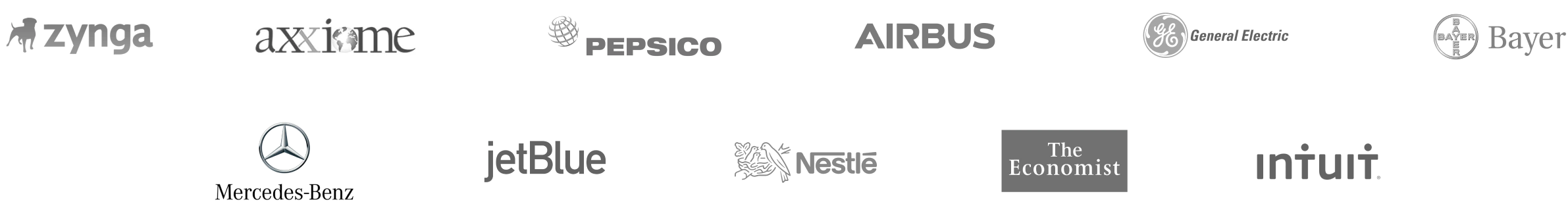Disaster-Proof your Software
Enterprise-ready Software Backup, Software Escrow, SaaS Escrow and Software Custodian solutions for software companies and their clients.
We support all popular developer platforms. 50+ Integrations available.

GitHub

Bitbucket

GitLab

Google
Cloud

Microsoft Azure

Amazon
Web
Services
Or explore our
Pricing OptionsTrusted partner of these great brands from around the world!
Are your software operations at risk?
Each year 42% of all businesses incur losses due to digital threats.
They thought they were safe too.
Data At Risk: Are You Prepared?
Don't let downtime disrupt your business. Loss from system failures costs companies an average of $5,600 per minute. This isn't just a risk—it's a costly daily reality.
Unanticipated system downtime can erase critical data in seconds.
Recovering from data loss often involves complex, time-consuming processes.
Delayed recovery leads to customer dissatisfaction, revenue loss and liabilities for your company.

Cyberattacks: A Digital Battleground
With 42% of cyberattacks targeting businesses like yours, the threat is not just probable; it's imminent.
Ransomware can lock you out of your own systems, halting your users and risking client data.
Hacking incidents can lead to the theft of proprietary code and sensitive client information.
Even a single breach can compromise sensitive client data and proprietary code.
Compliance and Legal: Regulatory Minefields
Safeguarding your business and client trust. With non-compliance costs averaging $14.8 million, the stakes in this regulatory landscape are incredibly high.
Failing to meet data protection regulations can lead to severe financial penalties and legal complications.
Compliance issues can disrupt client relationships and project timelines.
Your clients count on your adherence to industry standards to ensure their projects are legally secure and compliant.




Wondering about your disaster risk profile?
Use our free Risk Assessment report to understand your digital risks.
Or explore our
Pricing OptionsAt Codekeeper we know how critical your data and software systems are to your business.
We understand the anxiety and potential loss you face when thinking about possible disasters.
Our team of experts uses cutting-edge technology to ensure your business will recover or not even notice when a digital disaster catastrophe has occurred.


With over a decade of experience in disaster recovery, Codekeeper has helped countless businesses safeguard their most valuable digital assets and operations.
Your mission critical software assets should never have to be at risk.
These companies already secured their software continuity. Will you start today?


Your Action Plan
Your Roadmap to Disaster-Proof Software with Codekeeper:
Step 1: Quick Risk Check
Instantly assess your software risk landscape with our free and user-friendly tool.
Step 2: Tailored Expertise
Get a custom-fit recovery plan in a quick call with our experts.
Step 3: Easy Implementation
Invite your team and vendors to take advantage of our platform, activating your protection through our automated integrations.

Get our free risk assessment report template.
Simplifying Disaster Recovery
One centralized platform to handle all disaster recovery requirements for both software companies and their clients.
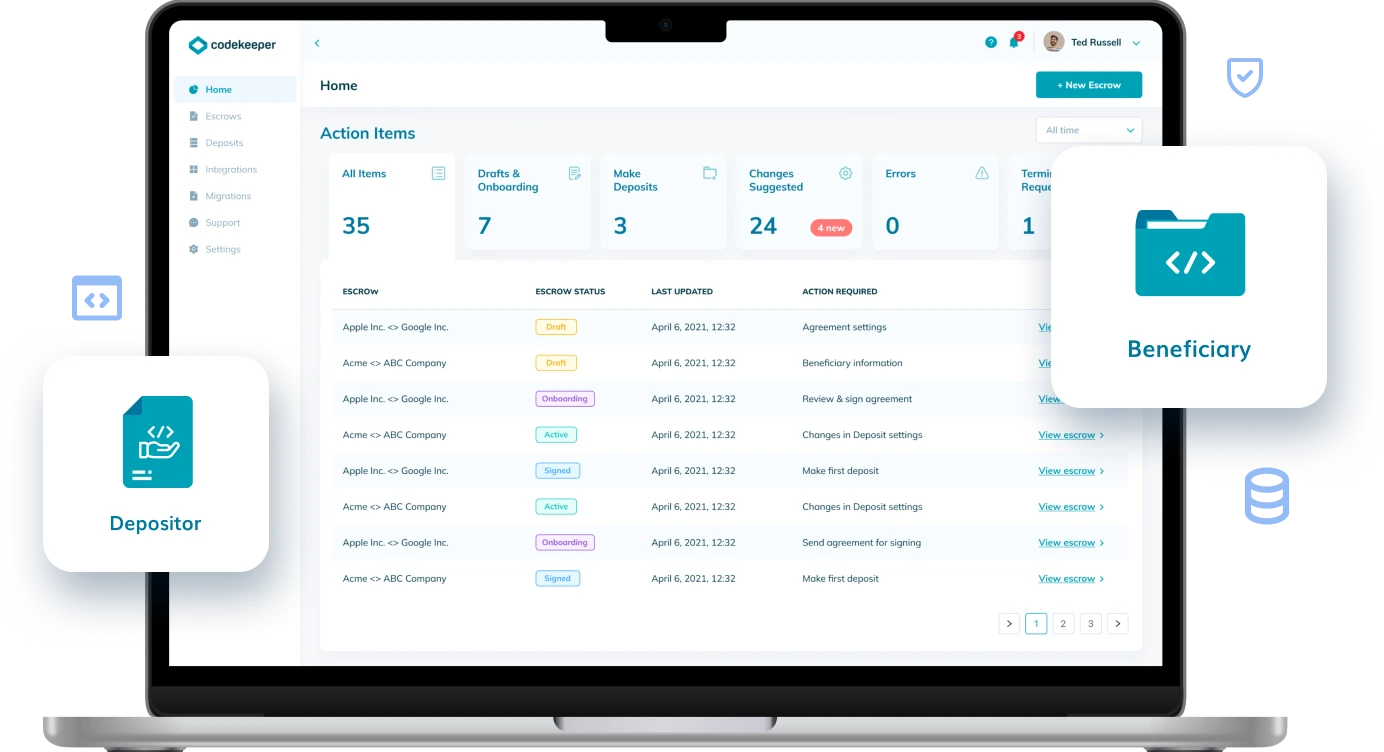
Learn more about solutions for quick recovery and full continuity that easily fit your existing workflows and procedures.
Explore Our Solutions

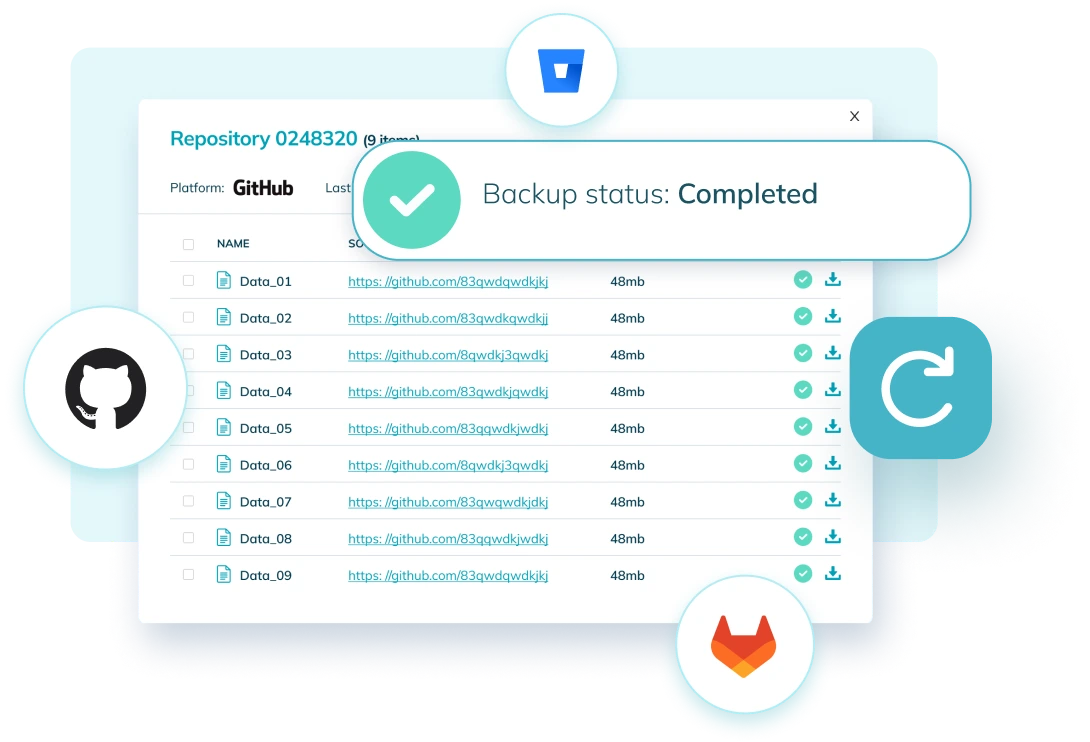
Software Backup
Securely store the source code of the applications that are the heart of your organization.
Fully Automated Source Code Backups
Integrations with all main software development platforms
Unlimited Repositories
From
$59 per month


Software Escrow
Securely store your software assets, ready for quick recovery when things go wrong.
Most recent version always deposited within 24 hours
Software escrow agreement included, incl. legal revisions
50+ Integrations available
AES-256 Encryption Security
From
$89per application per month




SaaS Escrow
Next level protection for cloud-native applications. Make sure your systems remain online when disaster strikes.
We keep your applications running for your users
Support any hosting environment
Support for 3rd party services & dependencies
From
$189per application per month


Software Custodian
Your responsibilities for your data don’t end, even if your company goes bankrupt. Our service covers the full life cycle of your data management for full compliance and control.
We manage your data when you can’t
Support for all major platforms and services
Guaranteed compliance and asset protection
Learn more
The Risk: A Digital Disaster Could Mean The End
In today’s world even a single digital disaster can lead to bankruptcy
You can’t afford to wait longer to make sure it doesn’t happen.
Loss of revenue
Every minute of downtime drains an average of $5,600 from your financial reserves.
Legal Repercussions
Face legal and regulatory challenges without proper solutions in place.
Compromised Data Integrity
A breach can irreparably tarnish the trust you've built with your clients.

Risks you can avoid today!
Modern business moves at a high pace and your software systems are of critical importance. Don’t get caught by a catastrophe when it’s easy to avoid these risks.
Counter Party Risk
Bankruptcy
Stolen Data
Lawsuits
Unplanned Downtime
Catastrophic events
Backup recovery problems
Misrepresentation
Hacking
Ransomware
Sabotage
And many more
Disaster-Proof Software
"Envision a business landscape free from the threat of data disasters, fortified by Codekeeper's resilience solutions."
For Software
Companies:

Enterprise-Ready Assurance:
Elevate your infrastructure to enterprise-grade resilience.
Client-First Security:
Offer impenetrable security, ensuring client data remains inviolable.
Regulatory Alignment:
Meet industry standards with confidence, sidestepping compliance concerns.
For Software
Clients:

Operational Excellence Guaranteed:
Achieve and maintain peak operational performance, no matter the challenge.
Business Continuity:
Shield your business operations, ensuring a seamless customer experience.
Regulation-Ready Posture:
Navigate the compliance landscape with ease and precision.
Together, we redefine digital safety, empowering your business to thrive in an unpredictable digital ecosystem.
Join these companies and protect your company today
 Get Started
Get Started
Best price guaranteed
No hidden costs
As seen on…
A few of the mentions we’ve received on the web.

Excellent service. This is easily the best way to handle it for both yourself and the client.


Codekeeper is a new service for creating escrow agreements for code, specifying the legal circumstances where source code can be accessed.


Source code escrow is a great service, and one that ALL developers who do client contract work should look into.

Frequently Asked Questions
-
What is Codekeeper?
- Codekeeper provides enterprise-ready software backup, software escrow, SaaS escrow, and data custodian solutions. We specialize in disaster-proofing software operations for companies and their clients, ensuring business continuity and compliance with cutting-edge technology.
-
How does Codekeeper protect businesses from digital threats?
- With over a decade of experience in disaster recovery, Codekeeper uses state-of-the-art technology to safeguard your most valuable digital assets against 42% of all businesses' common losses due to digital threats, ensuring your operations can recover or remain unaffected by digital disasters.
-
What solutions does Codekeeper offer?
- Codekeeper offers a comprehensive suite of solutions including Software Backup, Software Escrow, SaaS Escrow, and Data Custodian services, tailored to ensure your software assets are disaster-proof and your operations are secure and compliant.
-
How can I assess my software risk with Codekeeper?
- You can instantly assess your software risk landscape using our free and user-friendly tool. It's the first step in our roadmap to achieving disaster-proof software, providing you with a quick risk check of your current situation.
-
What is the process to get started with Codekeeper?
- Our process is simple and tailored to your needs: (1) Instantly assess your risk with our tool, (2) Get a custom-fit recovery plan in a quick call with our experts, and (3) Implement your plan easily with the support of our automated integrations inviting your team and vendors.
-
How does Codekeeper ensure compliance and security for its clients?
- Codekeeper ensures compliance and security by offering solutions that are aligned with industry standards, providing enterprise-grade resilience, impenetrable security for client data, and a regulatory-ready posture to navigate compliance landscapes with ease.
-
What industries benefit most from Codekeeper’s solutions?
- Our solutions are designed for any business reliant on digital assets, including those in finance, healthcare, government, defense, and more. We provide specialized attention to data handling and compliance requirements that remain critical even in disaster scenarios.
-
Can Codekeeper help if my vendor goes down?
- Yes, Codekeeper's solutions are designed to maintain operational continuity and compliance, even if a vendor goes down, by ensuring that your software and data management requirements are fully covered, without interruption.
-
Why is it important to have a disaster recovery plan?
- A disaster recovery plan is crucial to prevent loss of revenue, which can average $5,600 for every minute of downtime, mitigate legal and regulatory repercussions, and protect the integrity of client data, thus maintaining the trust and operational excellence of your business.
-
How can I join the companies already protected by Codekeeper?
- To join the growing number of companies secured by Codekeeper, start by using our free Disaster Recovery Planning tool to monitor your assets, identify risks, and structure mitigating measures. Contact us to further discuss how our solutions can be tailored to your specific needs.
Show more questions + Show less questions -
Haven’t found the answer you were looking for? Contact us


Disaster Recovery Planning
Use our free Disaster Recovery Planning tool to monitor your assets, identify risks and structure mitigating measures. All from one dashboard.
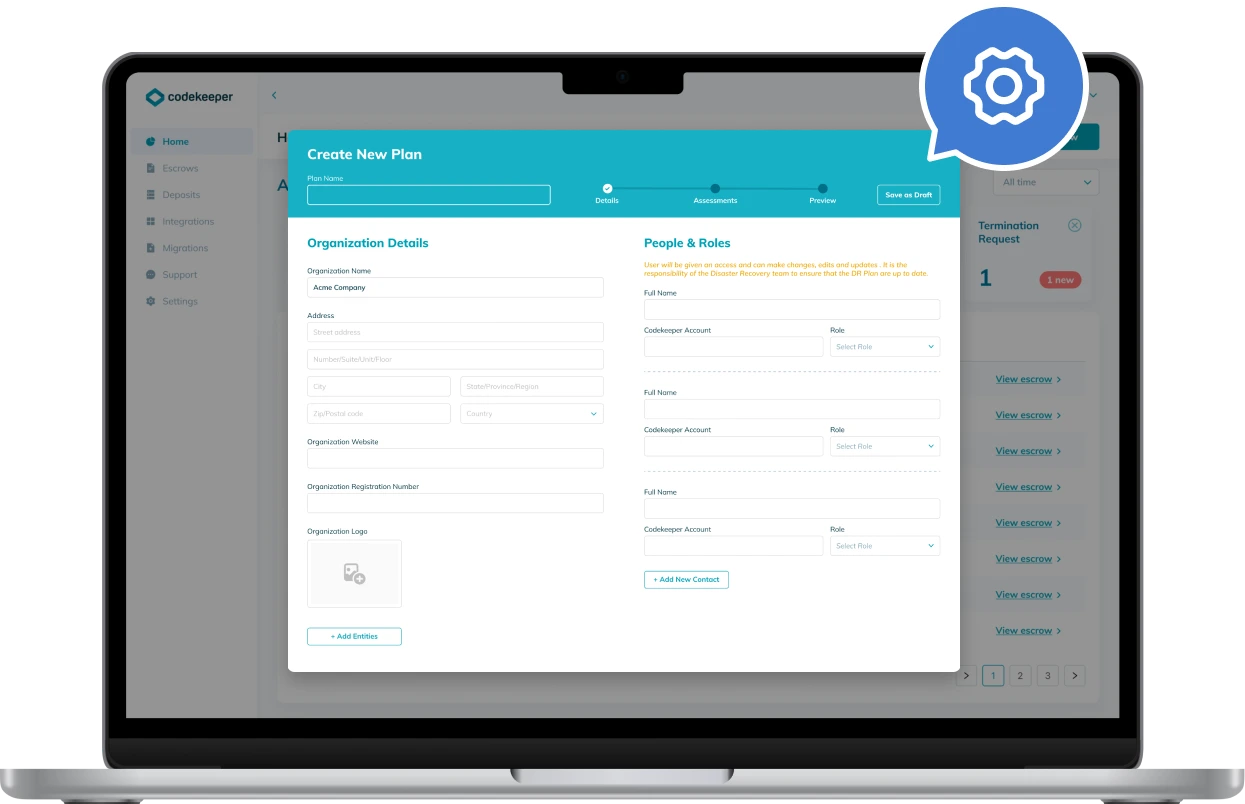
Disaster Recovery Planning Toolkit
Register for free and start planning your approach today.
Information Assets List
Internal and External Data Management Systems
Risk Register (use for your ISO27001/SOC2)
Risk Mitigation Methods
Or explore our
Pricing Options